What is Attack Surface Monitoring?
With digital transformation, cloud services, remote work arrangements, and the diversification of digital channels for various purposes, an organization's digital footprint is ever-expanding. This dynamic landscape has resulted in a broadened attack surface, making cybersecurity a complex challenge. While traditional security measures are effective in their own right, they must be equipped to deal with the ever-evolving threat landscape outside the security perimeter. The expansion of digital assets, including domain ownership shifts, expired SSL certificates, public staging environments, and unauthorized software downloads, further complicates this issue.
Attack Surface Monitoring is a critical cybersecurity methodology that aims to identify, inventory, classify, monitor, and prioritize all digital assets of an organization. It stands out due to its unique focus on improving existing security measures by detecting and closing security gaps often missed by traditional tools.
Why is Attack Surface Monitoring (ASM) Important?
Cybersecurity is only effective when you have visibility, as you can't protect what you can't see. The foundation of security is to understand your entire IT infrastructure and the associated risks. Continuous Attack Surface Monitoring offers real-time visibility into your constantly changing digital assets. It provides crucial insights into the what, when, who, and where of your organization's network, and it serves as a crucial element for proactive risk management and early threat detection.
Key Benefits of Attack Surface Monitoring
-
Real-time visibility of your digital footprint: Knowing the state, location, and security status of your digital assets is paramount. Attack Surface Monitoring provides constant visibility into your organization's assets. This helps you understand your digital footprint and the associated risks. As your attack surface changes, this real-time insight becomes increasingly important.
-
Continuous assessment of your security posture: With complete and real-time visibility into all digital assets, Attack Surface Monitoring, including continuous attack surface scanning, empowers you to assess your enterprise security posture at any given moment. This assessment helps determine your readiness to manage risks and respond to attacks effectively.
-
Manage security risk decisions: Proactive monitoring allows you to secure your environments in real-time as potential threats emerge. You can prevent attacks before they occur rather than merely reacting to them. Informed decisions about your digital assets' risks and potential entry points enhance your organization's cybersecurity posture.
-
Speed up remediation: Immediate awareness of vulnerabilities and weaknesses in your attack surface enables you to prioritize remediation efforts. You can address issues quickly, optimizing your cybersecurity defense.
-
Ensure compliance: Compliance regulations, such as GDPR, HIPAA, and PCI DSS, mandate the secure handling of sensitive data. Attack Surface Monitoring helps organizations identify non-compliance with these regulations and internal security policies, helping them avoid significant fines and reputational damage.
Attack Surface Monitoring Best Practices
While Attack Surface Monitoring is often a component of a broader Attack Surface Management (ASM) solution, it's important to implement certain best practices, whether as a part of your ASM security solution or as a standalone methodology:
-
Identify and prioritize: Due to the resource-intensive nature of continuous monitoring, organizations must prioritize their efforts. Assets should be sorted based on criticality, sensitivity of data, vulnerability, and business importance.
-
Establish a vulnerability patch process: Discover and monitor vulnerabilities on your assets. Establish a patch management procedure for the fast acquisition, testing, and installation of patches, ensuring that all vulnerabilities are addressed.
-
Have the endpoints in focus: Attack surface monitoring should contain endpoints, such as laptops, desktops, servers, mobile devices, and IoT devices. These endpoints are often the entry points for cyberattacks and need to be continuously monitored and protected.
-
Be alerted to changes: Automation and continuous scanning is key to efficient monitoring. Automation provides real-time alerts and notifications about changes in your infrastructure, enhancing your ability to react and make decisions about remediation.
Automate Attack Surface Monitoring with Trickest
Trickest's Offensive Security Orchestration Platform provides security teams with the tools and automation needed to effectively manage and monitor attack surfaces. By integrating a suite of over 25 ready-to-use attack surface management (ASM) workflows, Trickest offers the most powerful solution for identifying vulnerabilities and gaining insights into enterprise infrastructures. These workflows are built using top-tier open-source tools, creating an enterprise-grade system that simplifies attack surface mapping with just a few clicks.
Key aspects of Trickest's ASM solutions include:
- Continuous monitoring of total external infrastructure
- Instant notifications of changes in enterprise external infrastructure
The platform's low-code visual workflow editor allows for easy customization of workflows, enhancing existing methodologies and tailoring solutions to specific enterprise needs. Notable capabilities of Trickest for ASM include:
- Development of custom ASM workflows, enabling your specific asset and infrastructure enlightenment from an adversary's perspective.
- Stress-free execution infrastructure management, thanks to Trickest’s managed infrastructure that provides static IPs and handles execution setup and costs.
- Operational hyper-scalability to accommodate extensive digital landscapes and assets even with a nationwide volume, ensuring a complete security overview without the need for a large team of dedicated security specialists.
- A building framework for building other custom offensive security methodologies, supported by a library of over 300 open-source tools, Bash and Python scripting capabilities, integrations, and CLI.
- Addressing the Talent Gap: Amid a talent shortage in the cybersecurity domain, Trickest bridges the gap through advanced automation, allowing Offensive Security, Pentesting, Red & Purple teams to maximize security efforts with fewer resources.
Attack Surface Management Workflows
By using the following, most advanced ASM automated workflows, you can stay several steps ahead of the malicious hackers:
Asset Discovery & Vulnerability Scanning
Discover hostnames through passive and active techniques, enumerate web servers, scan for open ports, and discover vulnerabilities, disclosed secrets, exposed panels, and more.

Full Subdomain Enumeration
Uncover hidden subdomains with a collection of powerful active and passive enumeration tools seamlessly integrated into one workflow. No setup is required - you need to enter your targeted domain only.
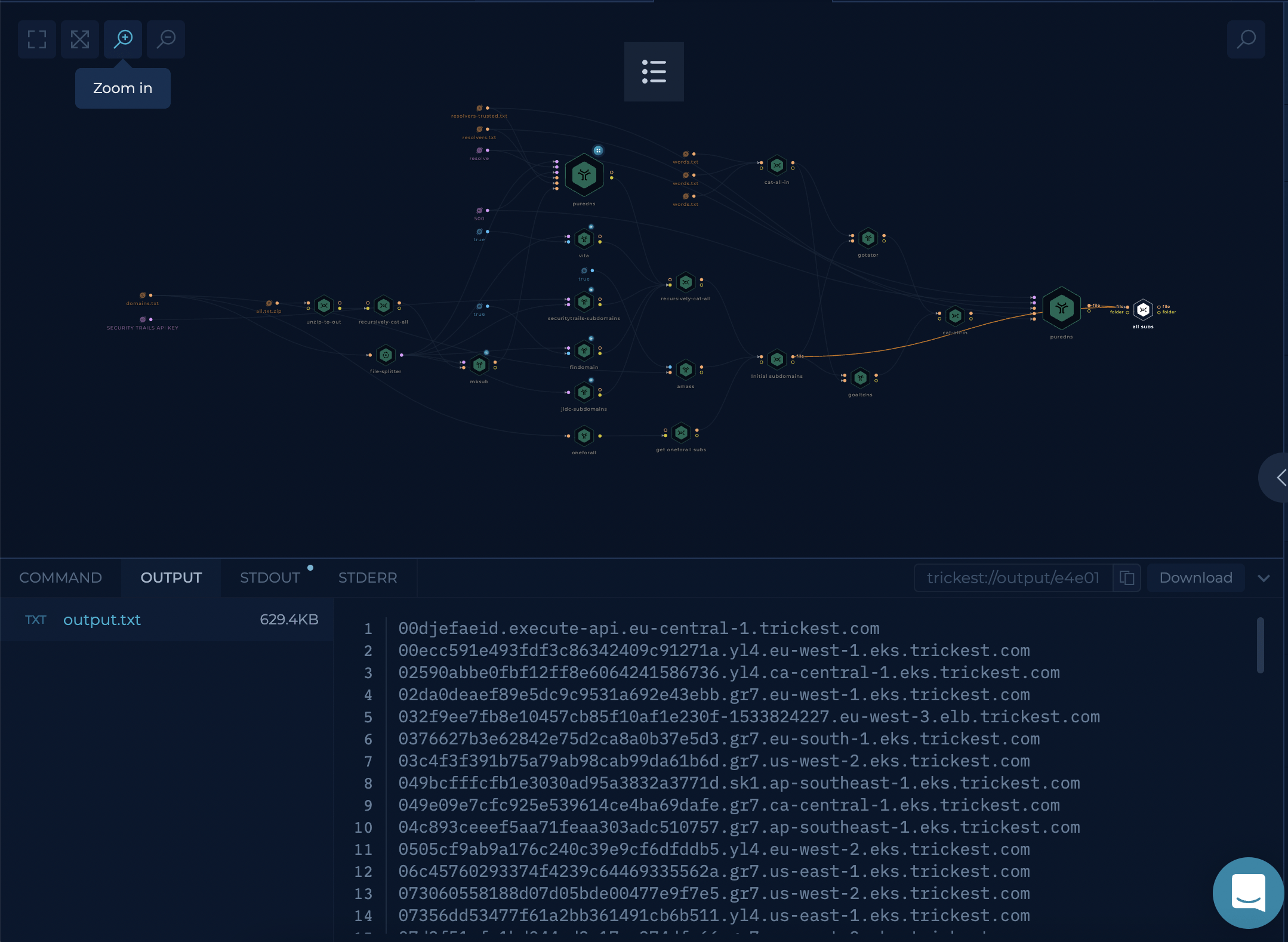
Inventory
Inventory 3.0, a workflow designed for thorough Attack Surface Management, is a game-changer for bug bounty hunters and security teams. This project aims to:
- Monitor 800+ Companies: Inventory 3.0 keeps a vigilant eye on over 800 companies, helping you stay ahead in the bug bounty game and ensuring you get all the new assets.
- Fast-Track Bug Bounty Programs: For bug bounty hunters, it's your secret weapon to adapt to new programs quickly, minimizing the learning curve.
- Enhanced Asset Visibility: Security teams benefit from heightened visibility into their assets, reducing the noise generated by automated tools and ensuring an efficient approach to managing their attack surface.
The Inventory 3.0 workflow operates through two components: Inventory 3.0 - Targets and Inventory 3.0. The Targets section consolidates data from various sources, creating a structured view of bug bounty programs. It streamlines data collection, transformation, and merges programs to eliminate redundancy. Community programs are also integrated, expanding coverage.
The Inventory 3.0 section collects data from targets.json, enabling data to run in parallel. It engages in passive enumeration, active enumeration, permutations, and the collection of previous results. The results are compiled and reported for an efficient bug bounty process.
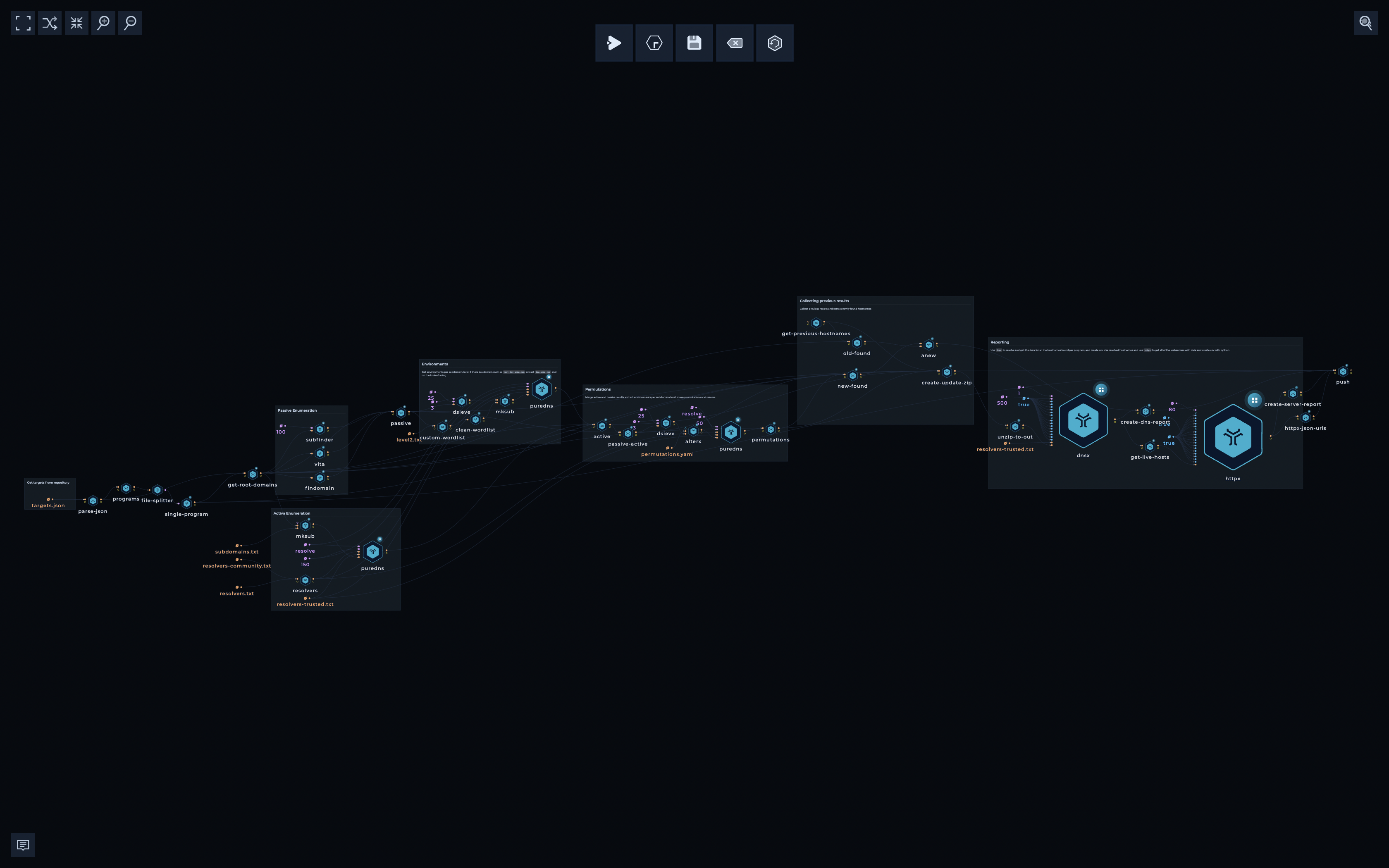
Other notable workflows for attack surface management that are available on a click:
- Levels-deep Subdomain Enumeration - Discover overlooked assets by enumerating subdomains, sub-subdomains, sub-sub-subdomains...
- Get IPs and CNAMEs - Get a list of IP addresses and CNAME values from a list of hosts.
- Resolve and port scan a list of hosts - Resolving host names first can lead to a faster port scan and give you more visibility into your target's IP space.
Discover more asm workflows in our product documentation.
Exploring Attack Surface Management Tools
In the Trickest Offensive Security Orchestration platform, the building blocks of all workflows are the world's most advanced community tools. There are hundreds of already integrated open-source tools widely used by ethical hackers and cybersecurity professionals for ASM.
You can integrate all open-sourced tools into the platform, and use them as building blocks for your custom workflows so you can build any type of automation. Here are only a few used in attack surface scanning highlighting their key features and functionalities.
- Amass - conducts network mapping for attack surface analysis and external asset discovery. Utilizes open-source information gathering and active reconnaissance methods.
- AlterX - a speedy and customizable vulnerability scanner powered by a straightforward YAML-based DSL (Domain Specific Language).
- puredns - a high-speed domain resolver and subdomain brute-force tool. It excels at accurately filtering wildcard subdomains and DNS poisoned entries.
- zgrab2 - a fast Go application scanner that provides detailed information on title status and content length.
- gowitness - A Golang-based utility for capturing website screenshots using Chrome Headless via the command line. Features a user-friendly report viewer for processing results. Compatible with Linux and macOS, with functional Windows support in progress.
You can explore more attack surface management tools in our documentation.
FAQ
What is Attack Surface?
The attack surface encompasses all the points, assets, or devices within a network that could potentially be targeted by an attacker seeking unauthorized access. This includes not only known assets but also those that are unidentified, third-party components, and even potentially malicious rogue infrastructure that could be vulnerable to exploitation.
What is the definition of Attack Surface Management (ASM)?
Attack surface management is a cybersecurity approach that involves discovering, monitoring, and managing an organization's attack surface. It includes the continuous assessment of assets, prioritizing vulnerabilities, and reducing risks in real time. ASM helps organizations remain alert and prepared against the constantly evolving digital threats.
What is Attack Surface Detection?
Attack Surface Detection is vital to managing an organization's attack surface. It involves actively monitoring and identifying changes and threats, enabling organizations to avoid potential cyber threats by detecting vulnerabilities and assessing risks in real-time. With Attack Surface Detection, organizations can proactively protect their assets and prevent cyber attacks.
How to Reduce your Attack Surface?
Reducing your attack surface involves a series of strategic measures designed to minimize potential vulnerabilities. This process includes eliminating unnecessary code, limiting access points, implementing strong user access protocols, and segmenting your network. By proactively managing and reducing your attack surface, you can enhance your organization's cybersecurity posture.
What are Attack Vectors?
Attack vectors are specific techniques and pathways that malicious actors use to infiltrate computer systems or networks. These vectors exploit vulnerabilities within an organization's attack surface, potentially leading to data breaches or cyberattacks. Understanding and addressing these attack vectors is essential for effective cybersecurity, as they represent the potential points of entry for attackers.
What are the key features of a robust attack surface monitoring platform?
A robust attack surface monitoring platform should offer several essential features to effectively identify, assess, and mitigate risks. These features often include real-time visibility, continuous assessment, comprehensive asset discovery, and the ability to prioritize vulnerabilities. The platform should also provide insights into compliance and risk management strategies.
How does continuous attack surface monitoring enhance an organization's cybersecurity?
Proactively monitoring the attack surface of an organization is crucial for its cybersecurity. Continuous assessment of assets, vulnerabilities, and potential threats enables real-time response and risk mitigation. With this approach, organizations can maintain robust security by staying ahead of evolving digital threats.
Why is addressing the attack surface outside of an organization's security perimeter crucial?
The attack surface extends beyond an organization's traditional security perimeter. With the increasing use of cloud services, remote work, and third-party vendors, many assets are nowadays scattered across the internet, making them vulnerable to malicious attackers. Addressing the attack surface beyond the perimeter is essential to prevent threats from these external vectors.